Securing Your IoT Devices - Making the Most of Particle's Security Features
Particle's Head of Security Mike Sheward teaches his top tips and tricks for using your Particle account in the most secure way possible.
Ready to build your IoT product?
Create your Particle account and get access to:
- Discounted IoT devices
- Device management console
- Developer guides and resources
Security works best when you take a holistic approach. After all, a skilled and determined attacker with a target in mind is not constrained by the societal barriers of our daily lives. If they want access to business data, they’ll happily leverage details from your personal accounts if they think that’ll help. Work-life balance doesn’t mean a thing to these people!
At Particle, we have a large and varied user base that includes individuals hosting their personal projects, students learning to work with hardware and code, scaling businesses building and shipping their first connected products, and some of the largest companies on the planet.
These user types have one thing in common: They all want and deserve security. In other words, they want to know that we at Particle are doing everything we can to keep their IoT products secure. You can read more about how we do that in our Security Architecture and Privacy Overview.
Ultimately, how you choose to use our platform, or any platform really, can have an impact on your overall security posture. This guide outlines our recommended best practices to maximize IoT security when building on Particle, taking into consideration just about everything you do from the day you sign up to the day you retire comfortably, having changed the world.
IoT Security Best Practices for All Particle Users
This section describes security best practices for all Particle users, whether they have one device or 100,000 devices.
Side Note: Check out our IoT Security Checklist to learn more about the common security threats connected products face and what to do about them.
Use A Password Manager
All passwords for online accounts should be strong and unique. The vast majority of account takeover events occur because the account holder reuses long-compromised password combinations that attackers can then replay.
But even a strong password isn't always enough.
The Particle Device Cloud enforces a password complexity policy based on the latest National Institute of Standards and Technology guidance—but honestly, you’ll never be able to remember your long and unique passwords without a password manager like 1password or Okta, both of which have Particle Device Cloud integrations.
Enable Two-Step Authentication
Two-step authentication is the most effective way to harden your Particle account, as it will block almost all password reuse and credential stuffing attacks. Follow the prompts to set it up as soon as you register.
Although you can leverage a two-step authentication app of your choice, we strongly recommend Authy.

Enabling two-step authentication in Particle Device Cloud.
Once you’ve enabled two-step authentication, you’ll want to securely store your recovery codes in case the device you use gets lost or damaged.
Oh, and enabling two-step authentication will also unlock a secret hardware discount reward code!
Know Your Network
For many of our users, Particle is a critical infrastructure provider. As such, Particle Device Cloud console connections are often considered privileged events and are not taken lightly.
We do all the right things in terms of transport layer encryption, but there are always risks when connecting from a network you don’t own or operate, with public and in-flight Wi-Fi being classic examples of "dirty" networks that may increase security risk.
Using a VPN you control (such as one provided by a business or one you’ve set up yourself) lets you ensure the network you're connecting from is safe. Free or commercial VPN providers require more research, since connecting to them may expose you to some risk.
Secure Your Access Token
A Particle access token is a sensitive thing that should be protected at all times. Later, we'll talk about how you can reduce the "blast radius" of access token compromise, but first, a general rule: Never expose your Particle access token. Ever.
That means:
- Never hardcode access tokens into source code. Instead, use a secrets manager to load in tokens at runtime.
- Never commit access tokens to a public source code repository. We proactively scan for tokens in the wild all the time. But if we can find them, hackers and bad actors can too, and they can gain unauthorized access to your systems. While we like to think we’re pretty quick, we can’t guarantee we’ll be the quickest!
Engage in General Secrets Management
One of the Particle platform's most powerful security features is the reverse connectivity from our devices to our cloud. Our devices have no open ports, allowing our cloud to act as a conduit to your own infrastructure so there's little need to store sensitive information on device firmware.
We recommend always keeping access tokens to third-party systems, passwords, and other sensitive values off devices and in the cloud. This allows you to quickly rotate values in the event of compromise or simply in support of identity and access management best practices. For example, an employee that leaves your company may be a potential threat actor if they still have an access token
Use Integrations That Leverage HTTPS-Only
When establishing an integration with the Particle Device Cloud, the default option is to require full HTTPS certificate validation and complete the connection over an encrypted TLS connection. In the 21st century, this option is available to everyone building on the Internet at little to no cost.
Because having a valid HTTPS certificate and an encrypted TLS/SSL connection are critical security measures to ensure your integration is targeting an authenticated endpoint and all your traffic is encrypted, we strongly recommend you only leverage integrations with HTTPS enabled. You can do this by setting the "enforce SSL" option in the integration configuration.
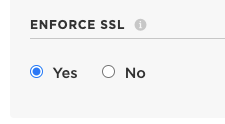
The ‘enforce SSL’ option in the integration configuration. And yes, this does also mean TLS.
Run the Latest Version of Particle Device OS
Unfortunately, Internet of Things devices don't have a great reputation when it comes to security. It can be extremely difficult to patch or update software, which leads to many connected products being sold, shipped, and forgotten. Forgotten devices become stale and eventually fall victim to legacy code and software vulnerabilities.
At Particle, we know a product's life cycle doesn't end the day the product is shipped. That’s why we support over-the-air device updates and ensure Particle Device OS—our open-source IoT operating system—is well maintained by our development team and the open-source community.
Striving to stay on the latest possible version of Particle Device OS is important not just to access the latest security updates and patches, but also to unlock features that’ll get you the most out of your device.
Best Practices for Accounts With Products
Next, we’ll take a look at specific best practices for any Particle accounts used to manage Particle-powered products.
Create a ‘Root’ Account for the Product Owner
"Least privilege" is a longstanding information security principle stating that a subject should always operate with the least amount of privilege required to perform the functions they are currently engaged in. The following recommendations are rooted (pun intended) in this important principle.
You're likely familiar with the "root" account in Unix-based operating systems—an all-powerful super-user that can affect everything on the system and should never be used for daily operations because of its immense power.
In the context of your Particle product, you can create a "root" user that acts as the product owner/administrator, then invite other team members or accounts to the product. Next, log out, delete all owner account access tokens, and use a lower-privileged user for subsequent tasks.
This reduces the owner account's exposure points and ensures that any subsequent access tokens or authentication clients created to support the product do not have the ability to perform owner account functions.

Separate Humans From Machines With API Users
There's a golden rule to remember when leveraging Particle access tokens or sets of client credentials with the "Full control" scope: They’ll always inherit the permissions of their creator.
For this reason, we recommend taking steps to maximize device security by separating humans from machines (service accounts) and sticking to that all-important principle of least privilege.
That means avoiding tying production credentials such as access tokens or Oauth clients to a human Particle user. After all, people have a tendency to come and go from organizations, and you’ll want to make sure you can completely revoke a former employee's platform access without impacting your product. That’s an identity and access management and overall cybersecurity best practice, after all!
You can do this by creating a "service account" that represents the services you’ll integrate with Particle, then scope that user's permissions appropriately. Multiple distinct service accounts can be used to ensure the principle of least privilege is applied as needed in different situations.
API users are perfect for the service account role, as these special, tightly scoped users are designed to be used programmatically and can be configured to perform a specific task. This tutorial walks you through the process of creating an API user.
Use a View-Only Account for Daily Monitoring
A view-only account role that allows you to observe but not touch the devices in a Particle product is great for simple fleet monitoring, whether you're presenting the Particle Console on a TV screen in your operations center or simply facilitating daily use when you don't have to routinely make changes to your product.
Quarantine Unrecognized Devices
When a device is added to a product, it will be able to download product firmware and trigger product webhooks. In order for a device to be given full access to product capabilities, the Particle Device Cloud must have a record of it being part of the product. If no record exists, the device is considered unrecognized.
Your product can be configured to handle unrecognized devices in two different ways: quarantine or auto-approve. We strongly recommend quarantine, which is the most secure and recommended option for handling unrecognized devices. By default, unrecognized devices will be quarantined to protect against potentially malicious actions from unrecognized devices unless you override this setting in your product's config page.
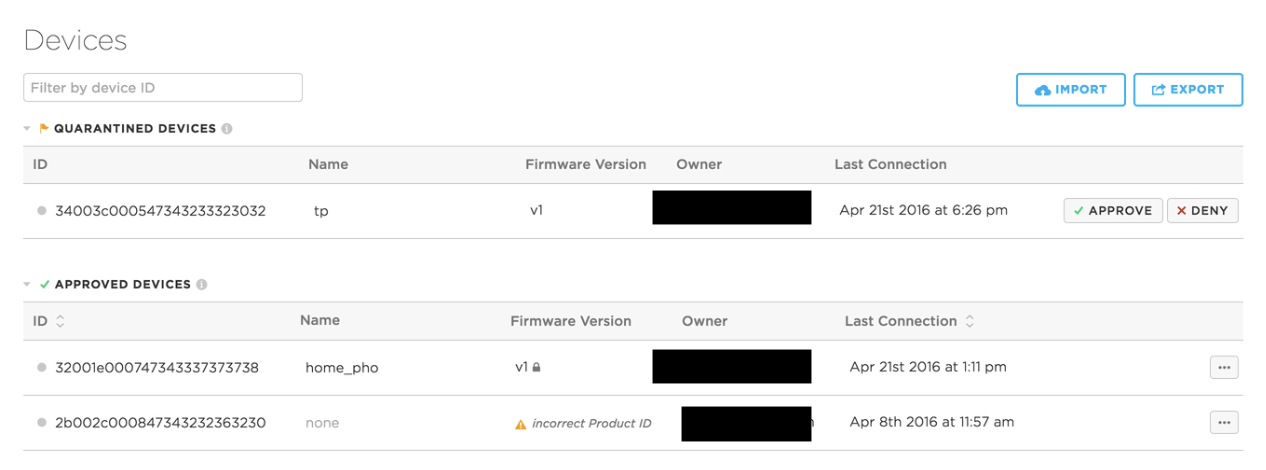
Quarantined devices are given limited permissions and must be approved before they can join the product.
Regularly Audit Your Integrations
Integrations are the way to get data off your Particle devices and into your own systems. Putting on our malicious actor hat, the integration system looks like a good place to go should we somehow be able to compromise a Particle account because there are no limits to the number of integrations that can be attached to a product.
A common technique used by malicious actors who compromise email accounts is to establish secretive forwarding rules to send sensitive emails to additional accounts under their control in case they lose access to their primary target account. These rules frequently go unnoticed for a very long time. When did you last check your own email account to see if it was forwarding to another destination?
Applying this threat model to Particle, we recommend routinely checking your integrations to make sure each one can be accounted for. Rest assured that we’ll also be keeping an eye on things behind the scenes, which includes automatically running any webhook URLs through our threat intelligence feeds.
Set and Monitor Cellular Data Limits
For cellular products, you can set a SIM data limit to control costs on new or existing SIM cards in the fleet. When a device is approaching its limit, we'll email you to advise you of your options.
If no action is taken, the device will have its cellular service paused for the remainder of the billing period. This, of course, can impact device availability—which, as a component of security, is worthy of mentioning here.
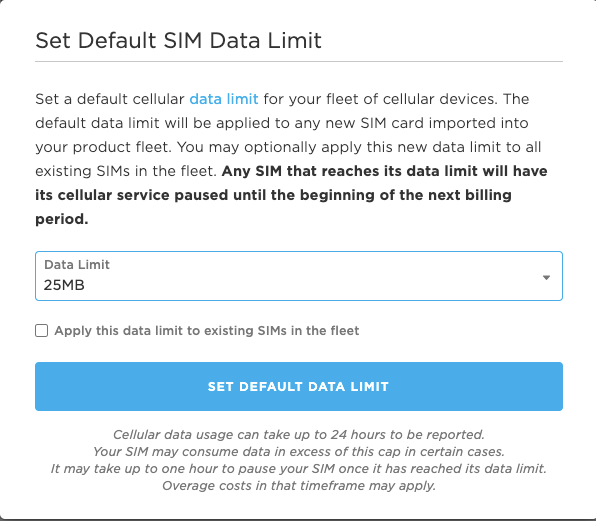
Set default SIM data limits, but be sure to monitor usage.
To avoid notification emails being caught by your spam filter, it's important to mark Particle as a trusted sender.
Use Development Devices for Testing
For a firmware engineer building a Particle product, it is important to rapidly iterate on new device firmware while still simulating the behaviors of production devices deployed in the field. Development devices allow you to do just that.
Development devices also allow you to keep your firmware in your product without having to spin up a copy in a personal development account. For Particle customers who have greater concerns about intellectual property security, this is an ideal approach to firmware development.
You can read more about development devices in the Particle Docs.
Respect Customer Privacy Rights
When it comes to our direct customers (i.e., the people building on the platform), we have processes in place to make sure we always do the right thing, which you can read more about in our privacy policy. We also want to provide the tools to help our direct customers do the right thing for our indirect customers (i.e., our customers' customers).
If you're storing product or customer information in Particle, be sure to integrate us into any privacy processes you establish. The Particle Device Cloud API makes it straightforward to remove a customer from your Particle account if, for example, they request to be forgotten.
We recommend building and testing processes to remove customer records and any other sensitive data that may tie your customers to a Particle device in the event that they wish to exercise their rights.
Best Practices for Enterprise Accounts
In addition to following the above recommendations, there are a number of extra steps that enterprise users of Particle can take to ensure the most secure platform use possible.
Regularly Audit Organizational and Product Access, Permission Levels, and MFA Controls
Enterprise users can take advantage of role-based access controls that provide user access to the entire organization, including all products. As stated earlier, we strongly recommend using the principle of least privilege when handing out access to team members.
Additional recommendations are to only grant organizational access to human users and to use API users at the product level to control access to each product function.
Finally, you should regularly review access at both the organization and product levels, ensuring every user has established two-step authentication and is using a strong, unique password managed by a password manager. Remember, you are only as strong as your weakest link.
The Teams view will show you which accounts don't have two-step authentication enabled.
Users should have their access promptly revoked after they leave your organization.
Use Long-Term Support Versions of Particle Device OS
Particle is constantly improving Particle Device OS by releasing new features that increase performance and improve our devices' standard behavior to better meet our customers' needs. However, we recognize that some of our customers value reliability over everything else—and for them, ongoing development and changes in behavior can create an undesired risk.
For these customers, Particle develops and deploys Long Term Support releases of Particle Device OS that deliver consistent behavior and stable performance for device applications over extended periods of time.
These LTS releases are independent branches of Particle Device OS that are feature-frozen in time, meaning they do not receive updates with new features, API changes, or improvements that change the function or standard behavior of the device. They are, however, supported by an extended support window to address critical bugs, regressions, security vulnerabilities, and issues that affect our wider enterprise customer community.
Read more about Device OS LTS.
Put a Canary in Your Firmware
Want a heads up that someone may be exploring your firmware unexpectedly? Enter the canary token, a secret that isn’t really a secret. Canary tokens are decoy values such as API keys and access tokens for various online services that you can include in your firmware; if someone discovers the token and attempts to use it, you will receive a notification.
Canary tokens are an excellent addition to any enterprise threat intelligence program that can serve as an early warning of a potential larger campaign against your company.
See https://canarytokens.org/generate for an example of a canary-generating tool.
Introduce Yourselves!
If your organization is building on Particle, the Particle security team is likely a key component in your incident response plan.
We'd love to meet you and learn how we fit in ahead of any potential incident, so the first time we interact will be in a low-stress situation that allows us to develop organization-specific response plans based on your needs. Please reach out through your customer success representative to set up an introductory call.
A Trusted Partner From Day One
Particle serves a variety of users across a range of industries. Whether you're just starting out with your first prototype or leveraging Particle to deploy your 1,000th unit, you can rest assured that you’re being backed by the people, processes, and technologies you need to stay secure.
Everything we observe and learn in the field is worked into our IoT Platform-as-a-Service and all its related products and services on an ongoing basis. Security is a journey, not a destination, and we hope you’ll join us on the trip.
Further Reading
Particle's wide variety of documentation and other materials relevant to our security program are available by request and, where applicable, under a non-disclosure agreement. Please reach out to your account executive if you would like to review any of the following:
- Latest SOC 2 Type II Report
- Particle security policies and procedures
- Latest vulnerability scan results
- GDPR/CCPA Third-party audit report
- Security architecture diagrams
- Latest penetration test report
- Rules of engagement for customer penetration testing
We welcome any questions you may have about our security or privacy practices—please reach out to your account executive, who will route your query appropriately.