A 2024 guide to IoT protocols and standards
Learn about the most common IoT protocols, their use cases, and how you can ensure you use the right one for your project.
Ready to build your IoT product?
Create your Particle account and get access to:
- Discounted IoT devices
- Device management console
- Developer guides and resources
When building an Internet of Things project, most stakeholders only care about getting data from their devices to their dashboards. Seldom do they think about how the data gets there, because they see that as the engineers’ responsibility.
In response, the engineers just shake their heads.
Understanding how your data is transmitted is essential to identify potential areas of optimization and improve your deployment’s performance. This is how you'll ensure that the technical solution to the business problem you’re trying to solve with IoT is the best it can be.
Protocols are the language that enables communication between devices and the cloud. Most protocols come with pros and cons—and while some work well for IoT, others do not.
This article will describe and compare the major protocols, discuss how they can be used in the IoT space, and detail how Particle finds the right protocols for your IoT deployment.
What are IoT protocols?
Before we dive into common IoT protocols, let's define the term "protocol" at a high level.
Protocols are a set of rules for transmitting data between electronic devices according to a preset agreement regarding information structure and how each side will send and receive data. Correspondingly, IoT protocols are standards that enable the exchange and transmission of data between the Internet and devices at the edge.
IoT protocols can be divided into two categories: IoT network protocols and IoT data protocols. Data protocols mainly focus on information exchange, while network protocols provide methods of connecting IoT edge devices with other edge devices or the Internet. Each category contains a number of protocols that each have their own unique features. We'll take a look at those next.
List of Common IoT Protocols
IoT Network Protocols
- Wi-Fi
- LTE CAT 1
- LTE CAT M1
- NB-IoT
- Bluetooth
- ZigBee
- LoRaWAN
IoT Data Protocols
- AMQP
- MQTT
- HTTP
- CoAP
- DDS
- LwM2M
Layers of the IoT protocol stack
"IoT protocol stack" refers to a hierarchy of software and hardware layers.
As Particle's Sr. Solutions Architect Dan Kouba phrased it, "It is all the things that sit in between the data being produced at the edge to the data being received by your systems."
The IoT network stack can be represented using the seven-layer OSI Network Model, starting from the physical layer at the bottom and ending with the application layer at the top. Specific protocols may represent only one layer or span many—regardless, they must be interoperable to ensure that the network functions as intended.
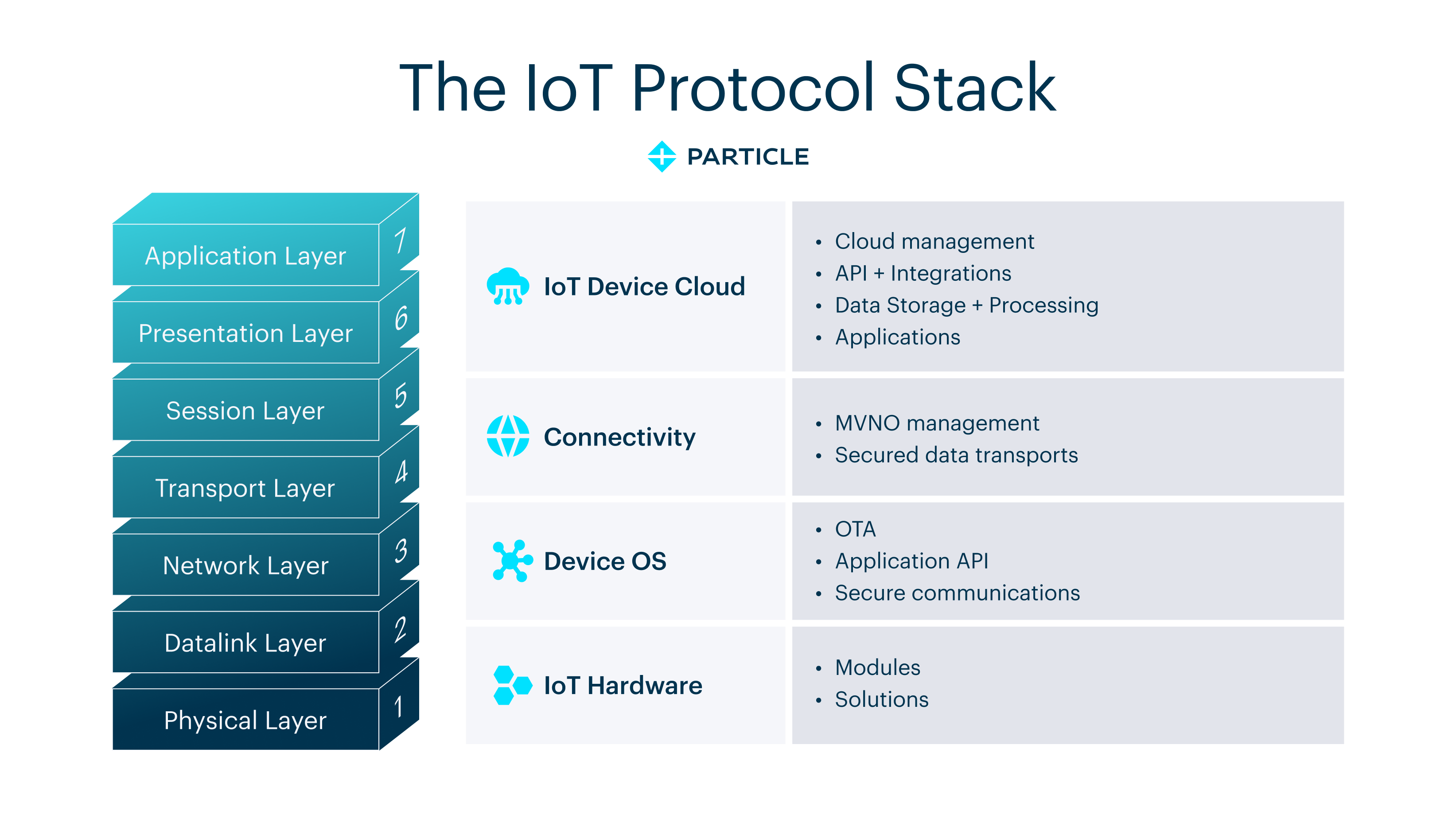
Next, let's take a closer look at each layer and its related functions.
Physical and Data Link Layers
The first two layers from the bottom—the physical and data link layers—define the physical connection of end devices to the network. More specifically:
- The physical layer receives unstructured raw data between devices and physical transmission media, then transmits the digital information into electrical, radio, or optical signals.
- The data link layer catches the data and detects/corrects any errors that may have occurred. This layer also defines the protocol for flow control, as well as establishing and terminating connections between two physically connected devices.
"The physical layer is the actual hardware that the electronics are on," explained Dan. "The data link layer represents how the modem negotiates with the cell tower—for example, to establish a communication channel between a device and the cell tower or other networking equipment."
Network, Transport, and Session Layers
The network, transport, and session layers facilitate data transfer over the connection, with a focus on logical addressing, traffic directing, error correction, flow control, congestion avoidance, session management, and reliability.
"From the user’s perspective, these layers are the protocols that run on top of the tunnel to facilitate communication," Dan noted. "What does that message look like? How is it formulated? How do I put data in it? How do we get data out of it?"
Presentation and Application Layers
The two layers at the top—presentation and application—deal with data formatting and the boundary between the data coming from devices in the field and a business application or database.
- The presentation layer transforms data into the form that is accepted by the application.
- The application layer—the layer closest to the user—typically identifies communication partners, determines resource availability, and synchronizes communication.
At this point in the process, all procedures are accomplished over an encrypted channel. Security applies to every layer in different ways and is often a function of the protocol being used. Once the data reaches the cloud, the systems will unpack it, analyze it, and make decisions accordingly before pushing each decision to the user's cloud platform.
IoT network protocols: What are they and what do you need to know?
Wi-Fi
Wi-Fi is a ubiquitous protocol that can be found almost anywhere—industrial plants, homes, commercial buildings, and even your neighborhood restaurants. This widely favored technology is able to transmit large volumes of data over reasonable distances. However, many low-power or battery-powered IoT devices are unlikely to use Wi-Fi due to its high power consumption rate.
Read our in-depth comparison of cellular vs. WiFi for IoT applications to learn more about when WiFi makes sense and when it doesn’t.
LTE CAT 1
LTE CAT 1 is a communication standard specifically designed for servicing IoT applications. Compared with other standards, it scales down bandwidth and communication demand to save power and cost for large-scale and long-range IoT systems. Though LTE CAT 1 performs inferiorly to 3G networks, experts predict that it will replace 3G as major U.S. carriers sunset 3G in 2022.
LTE CAT M1
LTE CAT M1—which can also be referred to as Cat-M—is a low-cost, low-power, wide-area network that specializes in transferring low to medium amounts of data. It was developed by the 3rd Generation Partnership Project as part of the 13th edition of LTE standard and is a core cellular IoT technology.
Cat-M stands out as a protocol option because it is compatible with the prevailing LTE network, meaning major carriers pivoting to it will not have to invest in new antennas.
Comparison: CAT M1 is considered a complementary technology to NB IoT. However, CAT M1 has a faster upload/download speed of 1 Mbps and a lower latency of 10 to 15 ms.
As of 2024, LTE CAT M1 and NB-IoT are now widely deployed and supported by major carriers worldwide, as the rollout has significantly progressed since 2022. This widespread availability has enabled the growth of large-scale, low-power IoT deployments across various industries.
NB-IoT
While the protocols detailed previously have been in application for a long time, Narrow Band-IoT is a new, fast-growing, low-power, wide-area technology intended to specifically target the needs of battery-powered IoT devices.
When compared to other cellular protocols, NB-IoT's advantages include improvements in power consumption, system capacity, and spectrum efficiency. For example, NB-IoT can connect huge fleets with up to 50,000 devices per network cell.
However, NB-IoT doesn’t come without challenges. The protocol has very limited bandwidth, which can slow or limit data transmission capabilities and make essential features like over-the-air updates difficult or impossible to achieve. Also, the protocol has seen limited rollout and support in worldwide geographies. While support is growing, fragmented availability is a risk to any IoT deployment.
Bluetooth
Bluetooth focuses on point-to-point, short-range communication of a relatively small amount of data. In the IoT space, Bluetooth is commonly used to connect small, battery-powered sensors to IoT gateways or to facilitate communication with a smartphone, eBike, or other smart device.
ZigBee
Ratified in the early 2000s, ZigBee stands out as a low-cost, low-power, and reliable wireless network technology. The standard is adaptable and supports multiple network topologies, including mesh networks, point-to-multipoint, and point-to-point. ZigBee is most commonly used in home or building automation settings.
LoRaWAN
Long-range wide area network—also referred to as LoRa—is a long-range, radio-wide networking protocol with low power consumption. Normally, LoRaWAN wirelessly connects multiple battery-operated devices to the Internet within regional, national, or global networks.
In the IoT field, LoRaWAN plays an important role in bidirectional communication, end-to-end security, localization, and mobility services.
IoT data protocols: What are they and what do you need to know?
AMQP
Known for its reliability and interoperability, Advanced Message Queuing Protocol is an open messaging standard. This protocol utilizes queues of data, enabling connected systems to communicate asynchronously and better handle issues like traffic spikes and poor network conditions.
Additional AMQP features include durable and persistent queues, federation and high-availability queues, clustering, and flexible routing. However, AMQP is known to be a verbose protocol in some circumstances.
Comparison: Compared with MQTT (discussed next), AMQP is more reliable and secure.
MQTT
Message Queue Telemetry Transport is a lightweight pub/sub messaging protocol suitable for connecting small, low-power devices.
This data protocol was designed specifically for IoT communication and requires minimal memory and processing power. On the wire, MQTT's bidirectional pub/sub architecture makes the protocol flexible and scalable for a wide variety of use cases and IoT system architectures.
Additionally, the MQTT protocol is designed with reliability and scalability in mind—security is provided via Transport Layer Security, and persistent sessions allow the protocol to adapt to poor network conditions and reduce connection time overhead.
HTTP
You might recognize this acronym as appearing at the beginning of every website address you type, as Hypertext Transfer Protocol is the foundation of data communication for the World Wide Web.
However, within the context of IoT applications, HTTP has many drawbacks. For instance, this protocol establishes a synchronous connection between two devices in order to transfer data—which presents a number of challenges for IoT deployments because devices and endpoints may not be online at the same time and connections may be unreliable due to network conditions.
Additionally, HTTP relies on transferring data in ASCII, which is an inefficient way to transmit the small bits of data often exchanged by IoT systems and requires more processing power to encode and decode messages at both ends.
Ultimately, while HTTP is a great choice for transferring website data, it is generally not a good choice for an IoT application.
CoAP
Constrained Application Protocol is used with constrained nodes and networks. This protocol is suited for IoT applications as it reduces the size of network packages, thereby decreasing network bandwidth overload. Other benefits of CoAP include improving the IoT life cycle, saving battery power and storage space, and reducing the amount of data required to operate.
DDS
Released in 2004, Data Distribution Service is a middleware architecture for real-time systems that focus on data communication between the nodes of a publication- or subscription-based messaging architecture.
DDS is mainly used under circumstances that require real-time data exchange—for example, autonomous vehicles, power generation, and robotics.
LwM2M
Lightweight Machine-to-Machine protocol is designed for remote management of M2M devices and related services. LwM2M reduces costs associated with low-power module deployment and equipping devices with faster IoT solutions. Learn more about M2M vs IoT.
Comparison: Note that the CoAP, LwM2M client initiates the connection to an LwM2M server that will use the REST API to manage the interfaces.
Why are protocols and standards important in IoT?
While this synopsis might seem like information overload, protocols are essential in IoT implementations.
"You want to make sure that whatever language your computers are speaking is really meant to be used for your use case," explained Dan. "There are lots of ways to establish communication between two machines, and picking the right one will give you advantages such as a low data rate."
Simply put, different protocols provide data in vastly different ways. For example, video call protocols might deliver data in a specific order all the time—something that's not necessarily guaranteed with other protocols—but may not be able to ensure that low data is passed between devices.
IoT security is another important element to take into consideration, as standardized IoT protocols can prevent further fragmentation and reduce the risk of security threats.
"Security requires some exchange of information to establish a secure tunnel, and doing that over certain protocols can be very data-intensive," said Dan. "Using the IoT-based protocols leveraged by Particle minimizes this intensity."
What protocols does Particle use and why?
At Particle, we mainly use CoAP and MQTT for our customers, as both minimize the amount of data transmitted and MQTT has a lot of institutional weight behind it.
As of 2024, we have expanded our protocol support to enable multi-radio networking. In addition to the previously supported CoAP and MQTT protocols, Particle now leverages LoRaWAN and satellite-based NTN (Non-Terrestrial Networks) protocols through partnerships with leading network operators like Helium, The Things Industries, Comcast's MachineQ, and Skylo.
"When Particle was created, we prioritized optimizing the amount of data used for each transaction via our cloud because that directly ties into the value we provide for our customers," Dan explained. "We give customers an allotted amount of data, and the more that they can do with that data, the more value they're able to extract from our solution."
Nowadays, many companies don't optimize the layers of the protocol stack, which tends not to be a direct driver of business value. This makes Particle's off-the-shelf solution an excellent choice for most use cases.
The beauty of our approach is that you don't have to think about choosing a protocol, as Particle's expert team will provide the stack and reference system for you. With this aspect taken care of, you'll have more time to focus on the two end layers of the stack—namely, what's happening at the edge and what's happening in the cloud.
According to Dan, "As long as you're transmitting your data, your data is relatively small, it's sent relatively infrequently, and there's not necessarily a need to have it explicitly ordered, Particle is going to be a great fit."